We Offer a User-friendly and Safe Platform

Register for a free account

Create an application

Begin verifying your users.
Easy to Use and Safe
ezto auth provides you with a single consolidated platform to make authentication a breeze.

Predefined Templates
Customized layouts for every industry and a lot of alternatives to browse.

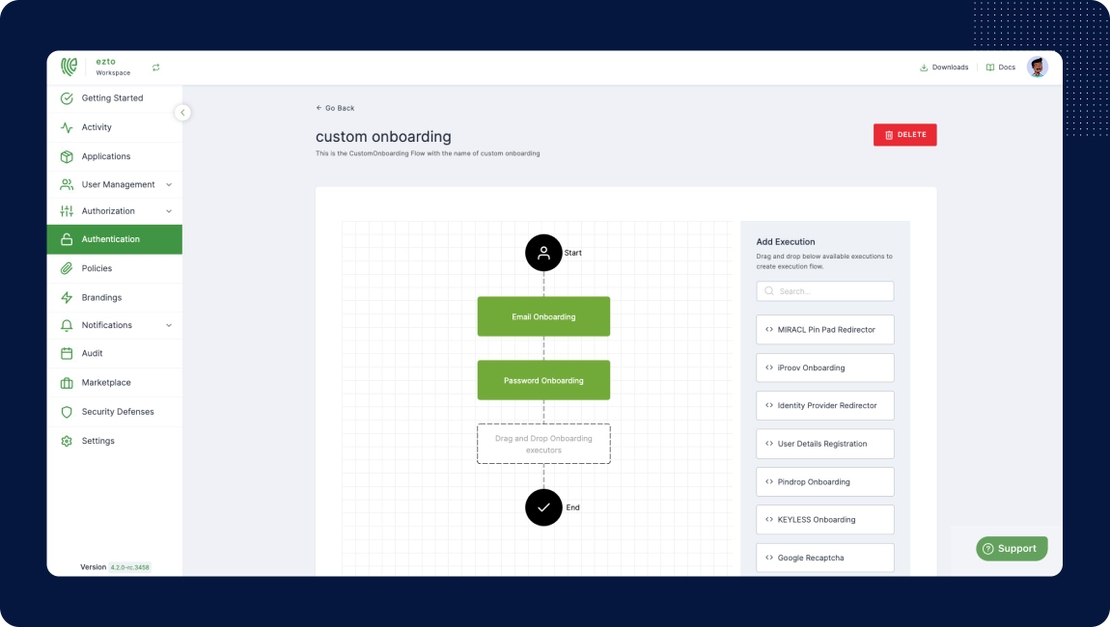
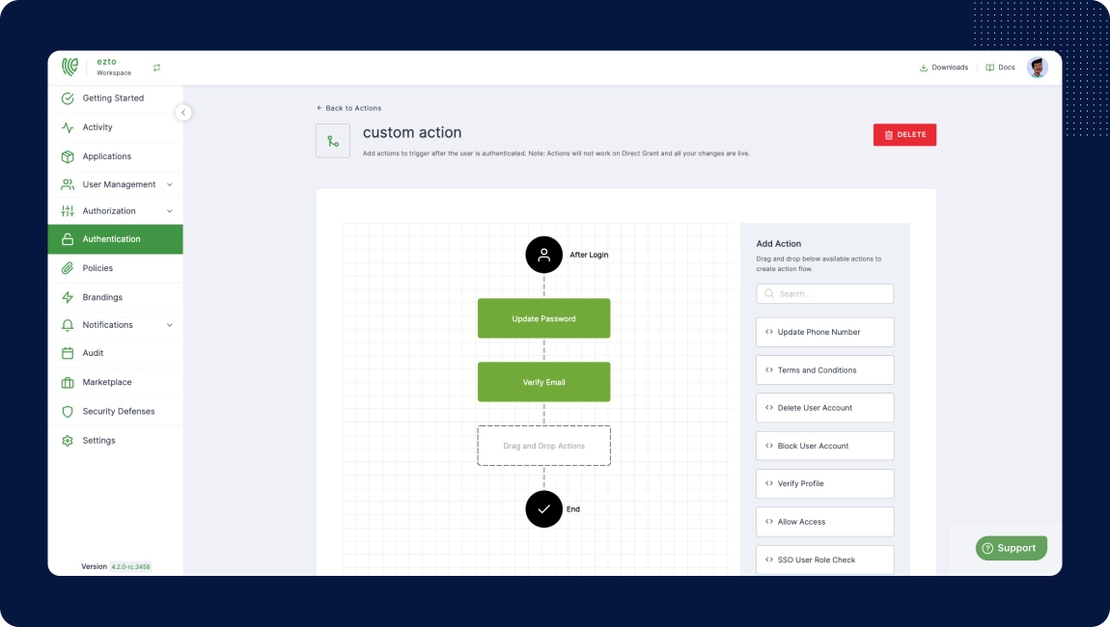
Custom Flows
On the off chance that you don't like our templates, no concerns. Still, you can define your custom flow with our intuitive maker.

Logs
Stream to your favourite provider, or view all your logs in the admin panel.

Create your own email templates and connect them to your preferred email service.

Themes
Themes tailored to your business's goals.

Profile Management
Admin dashboard allows you to manage users using interactive solutions.



Easy to Work With
Our bespoke admin interface is extremely easy to use and takes care of your authentication for you.

Full Featured
More than IAM is what we do. Our solution comes with everything that you'll need to manage.

Tailor Made Solutions
Provides the ability to request custom solutions in order to meet specific company needs.

Expert Support
When you're stuck, our specialists can aid, and they're also great at adapting your requirements.
3rd Party Integrations
Pricing Plan?
Premium Features, Smart Pricing - Pay Only for What You Use!
Want to Ask Something from Us?
What is ezto auth?
ezto auth is a secure authentication and authorization platform that prioritizes security while maintaining a user-friendly setup process. It effectively safeguards applications from potential threats such as compromised credentials and devices.
Our access security solution is designed to ensure the safety of all users, devices, and applications, enabling you to concentrate on your core activities with confidence in your security infrastructure.
Is it Open Source?
ezto auth is built as an extension of the open-source Keycloak, it's to note that ezto auth is not open-source itself. Open-source projects can sometimes experience delays and slow development progress. With new versions arriving infrequently and new features being introduced at a slow pace, making it challenging to prioritize complex yet crucial enhancements. As a result, ezto auth's choice not to be open-source allows for a more controlled and responsive development process, ensuring timely updates and prioritization of essential improvements.
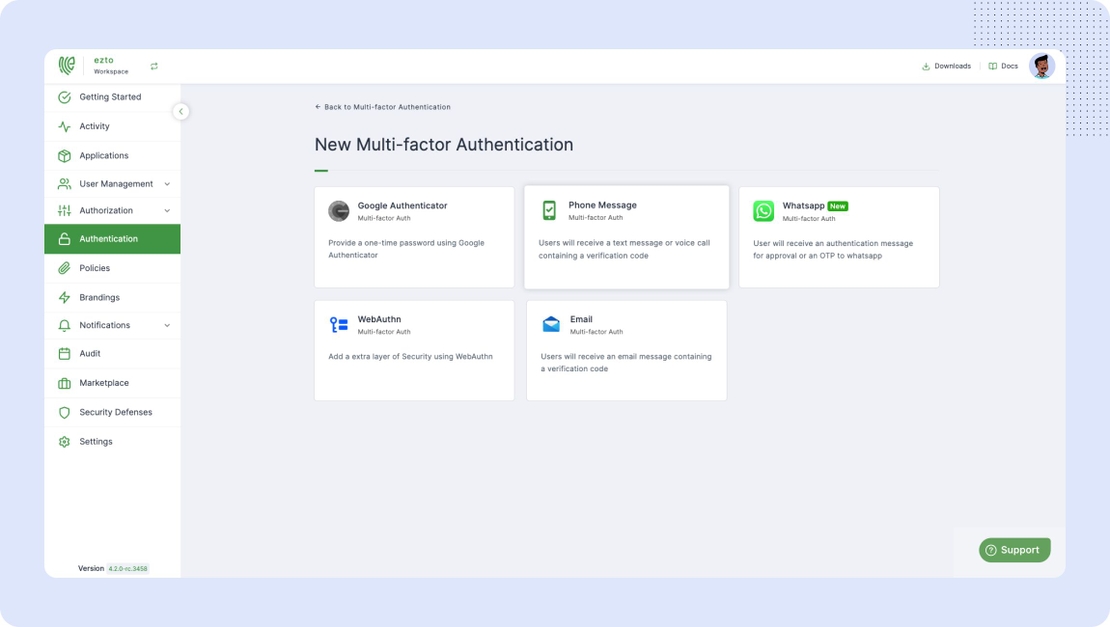
Does it Support 2FA or MultiFactor Authentication?
ezto auth provides robust security features through its support for both Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA). Users can choose from a variety of authentication methods, adding an extra layer of protection to ensure secure access to their accounts and sensitive information. This dual-layered approach significantly enhances the overall security posture of the authentication process.
Does it have cloud support?
Yes, we offer cloud support accessible upon request, as well as a cloud-hosted environment where you may try all of the available features until you're satisfied. You can install kubernetes at your cloud provider's convenience if Kubernetes is supported.
How can I request for new feature?
ezto auth enables users to directly request additional features through the contact sales page
Does ezto auth support on premise?
Cloud-based deployment offers greater flexibility compared to an on-premise design. However, on-premise deployment remains an option, and your choice depends on your specific circumstances and requirements.
Can I list my solution in ezto auth Marketplace?
We created the Marketplace to link our clients with service providers and builders that frequently deploy integrations. Your organisation will be promoted to our clients that are wanting to do more with their authentication pipeline by listing your integration with ezto auth.
Is it Vulnerability Checked?
Yes, first and foremost, ezto auth is always testing for newly reported vulnerabilities, and dependencies are evaluated against a comprehensive vulnerability database to offer clear and quick information on the severity and prevalence of a certain vulnerability.
Does it support LDAP?
ezto auth works with whatever authentication technique you choose, including signed certificates, LDAP, and other methods.
Stay in the loop – let's chat!
Got a unique need or a one-of-a-kind feature request? We're here to help! Reach out to our expert team anytime for assistance.